Hundreds of folks graduate from schools and universities every year with cybersecurity or laptop science levels solely to seek out employers are lower than thrilled about their hands-on, foundational expertise. Right here’s a have a look at a current survey that recognized some of the larger expertise gaps, and a few ideas about how these searching for a profession in these fields can higher stand out from the group.

Nearly each week KrebsOnSecurity receives at the very least one e mail from somebody searching for recommendation on how to break into cybersecurity as a profession. Typically, the aspirants ask which certifications they need to search, or what specialization in laptop safety would possibly maintain the brightest future.
Hardly ever am I requested which sensible expertise they need to search to make themselves extra interesting candidates for a future job. And whereas I at all times preface any response with the caveat that I don’t maintain any computer-related certifications or levels myself, I do converse with C-level executives in cybersecurity and recruiters on a common foundation and often ask them for his or her impressions of right this moment’s cybersecurity job candidates.
A typical theme in these C-level government responses is that a nice many candidates merely lack hands-on expertise with the extra sensible considerations of working, sustaining and defending the knowledge methods which drive their companies.
Granted, most individuals who’ve simply graduated with a diploma lack sensible expertise. However fortunately, a considerably distinctive side of cybersecurity is that one can achieve a honest diploma of mastery of hands-on expertise and foundational data via self-directed research and quaint trial-and-error.
One key piece of recommendation I almost at all times embrace in my response to readers entails studying the core parts of how computer systems and different gadgets talk with each other. I say this as a result of a mastery of networking is a elementary talent that so many different areas of studying construct upon. Attempting to get a job in safety with out a deep understanding of how information packets work is a bit like making an attempt to turn into a chemical engineer with out first mastering the periodic desk of components.
However please don’t take my phrase for it. The SANS Institute, a Bethesda, Md. based mostly safety analysis and coaching agency, lately performed a survey of greater than 500 cybersecurity practitioners at 284 totally different corporations in an effort to suss out which expertise they discover most helpful in job candidates, and that are most often missing.
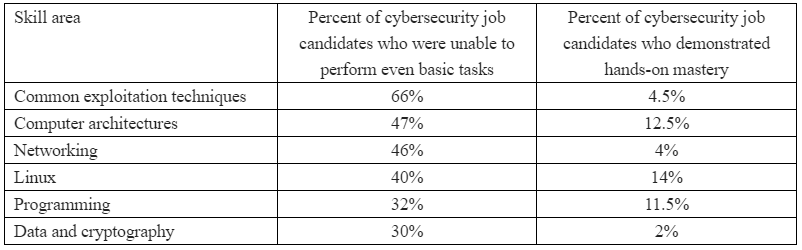
The survey requested respondents to rank numerous expertise from “essential” to “not wanted.” Totally 85 p.c ranked networking as a essential or “essential” talent, adopted by a mastery of the Linux working system (77 p.c), Home windows (73 p.c), widespread exploitation strategies (73 p.c), laptop architectures and virtualization (67 p.c) and information and cryptography (58 p.c). Maybe surprisingly, solely 39 p.c ranked programming as a essential or essential talent (I’ll come again to this in a second).
How did the cybersecurity practitioners surveyed grade their pool of potential job candidates on these essential and essential expertise? The outcomes could also be eye-opening:
“Employers report that scholar cybersecurity preparation is basically insufficient and are pissed off that they must spend months looking earlier than they discover certified entry-level staff if any may be discovered,” mentioned Alan Paller, director of analysis on the SANS Institute. “We hypothesized that the start of a pathway towards resolving these challenges and serving to shut the cybersecurity expertise hole can be to isolate the capabilities that employers anticipated however didn’t discover in cybersecurity graduates.”
The reality is, some of the neatest, most insightful and proficient laptop safety professionals I do know right this moment don’t have any computer-related certifications underneath their belts. Actually, many of them by no means even went to school or accomplished a university-level diploma program.
Slightly, they acquired into safety as a result of they had been passionately and intensely curious in regards to the topic, and that curiosity led them to be taught as a lot as they may — primarily by studying, doing, and making errors (heaps of them).
I point out this to not dissuade readers from pursuing levels or certifications within the subject (which can be a fundamental requirement for a lot of company HR departments) however to emphasise that these shouldn’t be seen as some form of golden ticket to a rewarding, secure and comparatively high-paying profession.
Extra to the purpose, with out a mastery of a number of of the above-mentioned expertise, you merely is not going to be a terribly interesting or excellent job candidate when the time comes.
BUT..HOW?
So what do you have to focus on, and what’s one of the best ways to get began? First, perceive that whereas there are a close to infinite quantity of methods to accumulate data and just about no restrict to the depths you possibly can discover, getting your arms soiled is the quickest option to studying.
No, I’m not speaking about breaking into somebody’s community, or hacking some poor web site. Please don’t do this with out permission. If you happen to should goal third-party companies and websites, stick to those who supply recognition and/or incentives for doing so through bug bounty programs, after which be sure to respect the boundaries of these packages.
In addition to, virtually something you need to be taught by doing may be replicated regionally. Hoping to grasp widespread vulnerability and exploitation strategies? There are innumerable free resources out there; purpose-built exploitation toolkits like Metasploit, WebGoat, and customized Linux distributions like Kali Linux which are effectively supported by tutorials and movies on-line. Then there are a quantity of free reconnaissance and vulnerability discovery instruments like Nmap, Nessus, OpenVAS and Nikto. This is on no account a full listing.
Arrange your individual hacking labs. You are able to do this with a spare laptop or server, or with older that’s plentiful and low cost on locations like eBay or Craigslist. Free virtualization instruments like VirtualBox could make it easy to get pleasant with totally different working methods with out the necessity of extra .
Or look into paying another person to arrange a digital server which you can poke at. Amazon’s EC2 services are a good low-cost possibility right here. If it’s internet utility testing you want to be taught, you possibly can set up any quantity of internet companies on computer systems inside your individual native community, equivalent to older variations of WordPress, Joomla or procuring cart methods like Magento.
Wish to be taught networking? Begin by getting a decent book on TCP/IP and actually studying the community stack and how each layer interacts with the other.
And when you’re absorbing this data, be taught to make use of some instruments that may assist put your newfound data into sensible utility. For instance, familiarize your self with Wireshark and Tcpdump, helpful instruments relied upon by community directors to troubleshoot community and safety issues and to grasp how community functions work (or don’t). Start by inspecting your individual community site visitors, internet searching and on a regular basis laptop utilization. Attempt to perceive what functions on your laptop are doing by what information they’re sending and receiving, how, and the place.
ON PROGRAMMING
Whereas with the ability to program in languages like Go, Java, Perl, Python, C or Ruby could or is probably not on the high of the listing of expertise demanded by employers, having a number of languages in your skillset just isn’t solely going to make you a extra enticing rent, it would additionally make it simpler to develop your data and enterprise into deeper ranges of mastery.
It is usually possible that relying on which specialization of safety you find yourself pursuing, sooner or later you’ll find your capability to broaden that data is considerably restricted with out understanding code.
For these intimidated by the thought of studying a programming language, begin by getting aware of fundamental command line instruments on Linux. Simply studying to write down fundamental scripts that automate particular guide duties may be a fantastic stepping stone. What’s extra, a mastery of creating shell scripts can pay good-looking dividends for the length of your profession in virtually any technical position involving computer systems (regardless of whether or not you be taught a particular coding language).
GET HELP
Make no mistake: Very like studying a musical instrument or a new language, gaining cybersecurity expertise takes most individuals a whole lot of effort and time. However don’t get discouraged if a given matter of research appears overwhelming at first; simply take your time and preserve going.
That’s why it helps to have assist teams. Severely. Within the cybersecurity business, the human aspect of networking takes the shape of conferences and native meetups. I can not stress sufficient how necessary it’s for each your sanity and profession to get entangled with like-minded folks on a semi-regular foundation.
Many of these gatherings are free, together with Security BSides events, DEFCON groups, and OWASP chapters. And since the tech business continues to be disproportionately populated by males, there are additionally a quantity cybersecurity meetups and membership teams geared towards girls, such because the Women’s Society of Cyberjutsu and others listed here.
Except you reside within the center of nowhere, chances are high there’s a quantity of safety conferences and safety meetups in your normal space. However even in case you do reside within the boonies, the excellent news is many of these meetups are going digital to keep away from the continuing pestilence that’s the COVID-19 epidemic.
In abstract, don’t depend on a diploma or certification to arrange you for the varieties of expertise employers are going to understandably count on you to own. That is probably not honest or accurately, but it surely’s possible on you to develop and nurture the talents that can serve your future employer(s) and employability on this subject.
I’m sure that readers right here have their very own concepts about how newbies, college students and people considering a profession shift into cybersecurity can greatest focus their time and efforts. Please be happy to hold forth within the feedback. I’ll even replace this submit to incorporate some of the higher suggestions.
Tags: Alan Paller, DEFCON Groups, How to Break Into Security, Kali Linux, Metasploit, Nessus, Nikto, Nmap, OpenVAS, OWASP, SANS Institute, Security BSides, TCP/IP, Tcpdump, Virtualbox, Webgoat, Wireshark, Women’s Society of Cyberjutsu
Supply: Source link
Comments
Post a Comment